Cybersecurity is a field that has exploded in popularity, and for good reason. In our increasingly digital world, data is paramount. Personal information is more vulnerable than ever, with data breaches and identity theft impacting millions. Remember the WannaCry ransomware attack a few years back? It crippled countless computers and highlighted the urgent need for robust digital defenses. From massive corporations to individuals, everyone is striving to protect their digital assets from cyber threats. You too can be part of this crucial defense. Cybersecurity isn’t just for tech giants; it’s relevant to personal computers, smartphones, and every device connected to the internet.
So, how do you dive into this vital field? This guide will walk you through the essential steps to learn cybersecurity, even if you’re starting from scratch.
Understanding the Fundamentals: What is Cybersecurity?
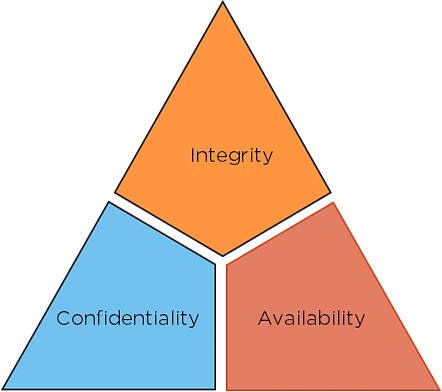
Before we explore how to learn, let’s solidify what cybersecurity actually is. Cybersecurity is the practice of protecting computer systems and networks from digital threats like theft, damage, and unauthorized access. It encompasses the technologies and processes implemented to ensure the confidentiality, integrity, and availability of information.
Cybersecurity is not just crucial for massive organizations and governments; it’s vital for hospitals, small businesses, and individuals alike. In today’s world, data is the lifeblood of almost every entity. If this data is compromised, the consequences can be devastating. To truly grasp cybersecurity, understanding the core principles is key, and that starts with the CIA Triad. For those looking to deeply specialize, exploring dedicated Cybersecurity Courses can provide structured pathways to expertise.
Enhance your expertise with the Advanced Executive Program in Cybersecurity. Gain practical skills and industry recognized certifications. Enroll now! 🎯
The CIA Triad: The Cornerstone of Cybersecurity
Every cybersecurity strategy is built on three fundamental principles, collectively known as the CIA Triad: Confidentiality, Integrity, and Availability. These have been the industry standard for computer security since the early days of mainframe computing.
Alt text: Diagram illustrating the CIA Triad in cybersecurity: Confidentiality, Integrity, and Availability, depicted as interconnected segments of a circle.
- Confidentiality: This principle ensures that sensitive information is accessible only to authorized individuals and processes. Think of military secrets or personal medical records – confidentiality is about keeping private data private.
- Integrity: Integrity focuses on maintaining the accuracy and completeness of data. It ensures that information is not altered or tampered with by unauthorized means. Imagine preventing a malicious actor from changing financial transaction records.
- Availability: Availability means that systems, data, and resources are accessible to authorized users whenever they are needed. This is about ensuring uptime and preventing disruptions to services, like keeping a website online during peak hours.
Understanding the CIA Triad provides a solid foundation as you delve deeper into the various domains of cybersecurity.
Areas of Specialization in Cybersecurity: What Can You Learn?
If you are considering a career in cybersecurity, knowing the different specializations can help you focus your learning. Cybersecurity is a broad field with many exciting paths. Here are key areas to explore:
- Access Control Systems and Methodology: Learn how to protect critical system resources from unauthorized access and modification. This involves understanding authentication and authorization mechanisms.
- Telecommunications and Network Security: Dive into securing communication channels, network protocols, and network services. This includes learning about firewalls, VPNs, and intrusion detection systems.
- Security Management Practices: Discover how to handle system failures, disasters, and service interruptions effectively. This area covers incident response, business continuity, and disaster recovery planning.
- Security Architecture and Models: Focus on designing and implementing security policies and procedures. This involves policy creation, risk assessment, and security framework development.
- Law, Investigation, and Ethics: Understand the legal and ethical aspects of cybersecurity, including cybercrime laws, digital forensics, and ethical hacking principles.
- Application and System Development Security: Learn to build secure applications and systems by implementing security at every stage of development. This includes secure coding practices and vulnerability testing.
- Cryptography: Master the art and science of encryption to protect data confidentiality and integrity. This involves learning about different encryption algorithms and their applications.
- Computer Operations Security: Cover all aspects of security while computers are running, including monitoring, logging, and security event management.
- Physical Security: Address the physical protection of hardware and infrastructure, including access controls, surveillance, and environmental security.
Become an industry-ready professional with the Advanced Executive Program in Cybersecurity. Gain insights from industry experts and enhance your career prospects. Enroll today! 🎯
Basic Cybersecurity Terminology: Building Blocks of Knowledge
To start your learning journey, familiarizing yourself with fundamental cybersecurity terms is crucial. Here are some essential terminologies:
1. Network
A network is simply a connection between two or more computers that allows them to communicate and share resources.
Alt text: Illustration of a computer network showing multiple devices connected through a central hub, representing data flow and communication.
2. Internet
The Internet is a global network connecting computers worldwide through routers and servers, enabling communication and data exchange across vast distances.
3. Internet Protocols
Internet protocols are sets of rules that govern how data is transmitted and received over the internet, ensuring smooth and controlled data flow. These protocols are fundamental to how the Internet functions.
4. IP Address
An Internet Protocol address (IP address) is a unique numerical label assigned to each device connected to a computer network that uses the Internet Protocol for communication. It looks like this: 192.168.1.1.
5. MAC Address
A Media Access Control (MAC) address is a unique hardware identifier assigned to a network interface controller (NIC) for communication within a network. It’s usually a 12-digit hexadecimal number, like: 00-1A-2B-3C-4D-5E.
Did You Know? 🔍
In the second quarter of 2024, organizations faced an average of 1,636 cyber attacks weekly, a 30% increase year-over-year, highlighting the escalating threat landscape.
6. Domain Name System (DNS)
Think of DNS as the internet’s phonebook. It translates human-readable domain names (like google.com) into IP addresses that computers use to locate each other.
Alt text: Diagram illustrating a DNS server lookup process, showing a user’s computer querying the DNS server to translate a domain name into an IP address.
7. DHCP
Dynamic Host Configuration Protocol (DHCP) automatically assigns IP addresses and other network configuration parameters to devices when they connect to a network, simplifying network management.
Alt text: Diagram showing a DHCP server automatically assigning IP addresses to various devices connecting to a network.
8. Router
A router is a networking device that forwards data packets between computer networks. Routers direct network traffic to ensure data reaches its intended destination efficiently.
9. Bots
Bots are software programs that automate tasks. In cybersecurity, “bots” often refer to malicious programs that can control your computer without your knowledge, often used in botnets for large-scale attacks.
Develop skills for real career advancement with CISSP Certification Training Course. Explore program now!
Common Types of Cyber Attacks: What to Watch Out For
Understanding the types of attacks is crucial for effective cybersecurity learning. Most cyber attacks are motivated by financial gain, with attackers seeking ransom, financial theft, or causing financial damage to targets. Other motives include disrupting operations, damaging reputations, or political maneuvering.
Here are five common types of cyber attacks you should learn about:
- Distributed Denial of Service (DDoS)
- Man-in-the-Middle (MITM)
- Email Attacks
- Password Attacks
- Malware Attacks
Let’s delve into each of these attack types:
1. Distributed Denial of Service (DDoS)
A Distributed Denial of Service (DDoS) attack aims to overwhelm a target system with traffic, making it inaccessible to legitimate users. Attackers use botnets—networks of compromised computers—to flood servers with requests, causing them to crash.
Alt text: Diagram illustrating a DDoS attack, showing multiple bots in a botnet overwhelming a target server with excessive traffic.
2. Man-in-the-Middle (MITM)
A Man-in-the-Middle (MITM) attack occurs when an attacker intercepts communication between two parties without their knowledge. Imagine doing online banking:
Alt text: Diagram illustrating the initial stage of a Man-in-the-Middle attack, showing a user connecting to a bank server.
During a transaction, you enter your credit card details and PIN. In a MITM attack, the attacker intercepts this communication:
Alt text: Diagram illustrating a Man-in-the-Middle attack, showing an attacker intercepting data transmission between a user and a bank server to steal sensitive information.
The attacker can then steal your credentials and financial information.
3. Password Attacks
Password attacks are techniques used to crack or recover passwords. Common types include:
- Dictionary Attack: Using a list of common words (dictionary) to guess passwords.
- Brute Force Attack: Trying every possible combination of characters until the correct password is found. This is time-consuming but effective.
- Keylogger: Malware that records keystrokes, allowing attackers to capture passwords as they are typed.
- Shoulder Surfing: Observing someone typing their password over their shoulder.
- Rainbow Table Attack: Using precomputed hash values to quickly find passwords.
4. Email Attacks
Understanding how email works is essential to recognize email attacks. When John sends an email to Jack:
Alt text: Diagram illustrating the email sending process, showing the path of an email from sender to receiver through email servers and DNS servers.
The email travels from John’s email server to the DNS server to find Jack’s server IP address, then to Jack’s email server, and finally to Jack’s inbox. Common email attacks include:
-
Phishing: Deceptive emails designed to trick recipients into revealing sensitive information. Example:
Alt text: Screenshot of a phishing email example, prompting users to click a link and enter personal details under a false pretense.
These emails often mimic legitimate organizations to steal credentials.
-
Spoofing: Attackers forge email headers to make emails appear to come from a trusted source:
Alt text: Screenshot of a spoofing email example, appearing to be from a legitimate sender but requesting sensitive information like passwords.
Always verify the sender’s authenticity.
-
Malicious Attachments: Emails containing infected files (documents, images, etc.) that deploy malware when opened:
Alt text: Screenshot of an email example with a malicious attachment, warning users about the dangers of opening unknown attachments.
Only download attachments from trusted sources.
5. Malware Attacks
Malware is malicious software designed to harm computer systems. Types of malware include:
- Virus: Malicious code that replicates by attaching itself to other programs or documents, spreading when infected files are shared. Example: Melissa virus.
- Worms: Self-replicating malware that spreads independently across networks without needing to attach to a host file. Example: W32.Alcra.F worm.
Learn from leading cybersecurity experts with the Cyber Security Expert Master’s Program. Explore the program!
Functions of Malware
Malware can perform various malicious actions:
- Overwhelming System Resources: Malware, especially worms, can consume excessive system resources, leading to slowdowns and crashes.
- Creating Backdoors: Malware can create backdoors, allowing attackers persistent access to compromised systems for future attacks or data theft.
- Disabling Security Functions: Some malware disables antivirus software and security updates, leaving systems vulnerable to further infections.
- Creating Botnets: Malware can turn infected computers into bots, which are then used to form botnets for large-scale attacks like DDoS.
Sources of Malware
Malware can spread through various means:
- Removable Media: Infected USB drives, CDs, and DVDs can spread malware when connected to systems.
- Documents and Executable Files: Malware can be hidden in seemingly harmless files, activating when opened.
- Internet Downloads: Downloading files from untrusted websites can lead to malware infections.
- Network Connections: Unsecured networks can be exploited to spread malware.
- Email Attachments: Opening malicious email attachments is a common way to get infected.
- Malicious Advertisements (Malvertising): Clicking on untrusted ads can lead to malware downloads or redirects to malicious sites.
Advance your cybersecurity skills with the Cyber Security Expert Masters Program—comprehensive training in critical cybersecurity domains. Enroll Now! 🎯
Cybersecurity Job Roles: Career Paths to Explore
Understanding potential career paths can motivate your learning journey. Here are some top cybersecurity job roles:
- Chief Information Security Officer (CISO): Leads and manages an organization’s entire IT security strategy.
- Forensic Computer Analyst: Investigates cyber incidents, analyzes digital evidence, and helps in post-breach recovery.
- Information Security Analyst: Protects computer systems and networks, implements security measures, and monitors for threats.
- Penetration Tester (Ethical Hacker): Simulates cyber attacks to identify vulnerabilities in systems and networks.
- IT Security Engineer: Plans, implements, and manages security measures to protect data and systems from cyber threats.
- Security Architect: Designs and oversees the implementation of an organization’s network and system security architecture.
- Security Systems Administrator: Installs, manages, and troubleshoots security systems and tools.
- IT Security Consultant: Provides expert advice and guidance to organizations on improving their cybersecurity posture.
Cybersecurity Certifications: Validate Your Skills
To enhance your career in cybersecurity, consider pursuing relevant certifications. Top certifications include:
- CompTIA Security+: Entry-level certification covering fundamental security skills.
- Certified Ethical Hacker (CEH): Focuses on ethical hacking and penetration testing techniques.
- Certified Information Systems Security Professional (CISSP): Advanced certification for security professionals managing and directing security programs.
[Include video here, if available, as mentioned in original Vietnamese article]
The demand for cybersecurity professionals is rapidly growing as technology advances and cyber threats become more sophisticated. Cybersecurity is a complex yet rewarding field that requires continuous learning and adaptation.
This guide provides a starting point for your cybersecurity learning journey, covering fundamentals, key terminologies, attack types, and career paths. If you are ready for a challenging and impactful career, explore comprehensive programs like Simplilearn’s Cybersecurity Expert Masters program, which offers in-depth training from beginner to advanced levels, equipping you with the skills needed to succeed in this critical field. Start your cybersecurity learning adventure today!