Cyber security for beginners can seem daunting, but with the right approach, it’s an achievable and rewarding goal, especially with resources from LEARNS.EDU.VN. This guide provides a structured path to acquiring essential cyber security skills, focusing on key concepts and practical applications, ensuring you’re well-prepared to navigate the digital landscape safely. Let’s explore together and find out more!
1. Understanding the Basics of Cyber Security
Before diving into the specifics, it’s crucial to understand what cyber security encompasses and why it’s vital. Cyber security involves protecting computer systems, networks, and data from digital attacks. Given the increasing reliance on technology, cyber security has become indispensable for individuals, businesses, and governments alike.
1.1 Defining Cyber Security
Cyber security refers to the practice of protecting digital information and assets from unauthorized access, use, disclosure, disruption, modification, or destruction. It involves a combination of technologies, processes, and practices designed to safeguard networks, devices, programs, and data from cyber attacks. According to a report by Cybersecurity Ventures, cybercrime is projected to cost the world $10.5 trillion annually by 2025, underscoring the critical importance of cyber security.
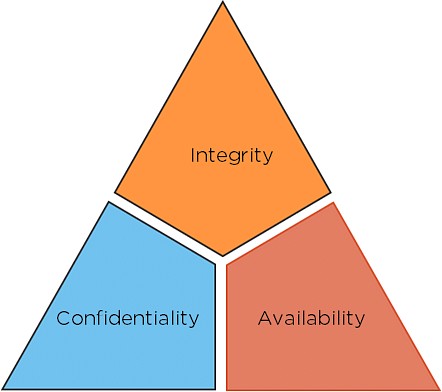
1.2 Key Principles: The CIA Triad
The CIA triad forms the cornerstone of cyber security, ensuring data and systems are protected through three essential principles:
- Confidentiality: Ensures that information is accessible only to authorized individuals or entities. This is achieved through methods like encryption, access controls, and secure data storage.
- Integrity: Guarantees the accuracy and completeness of information. It involves preventing unauthorized modification or deletion of data through techniques like hashing, version control, and access permissions.
- Availability: Assures that authorized users have reliable and timely access to information and resources. This is maintained through redundancy, disaster recovery plans, and robust infrastructure.
1.3 Why Cyber Security Matters
Cyber security is essential due to the ever-increasing threat landscape. Cyber attacks can result in significant financial losses, reputational damage, legal liabilities, and disruptions to critical infrastructure. A report by IBM found that the average cost of a data breach in 2023 was $4.45 million, highlighting the financial impact of cyber incidents.
1.4 Common Cyber Threats
Understanding the types of threats you’ll be facing is the first step in learning how to defend against them. Here’s a brief overview of some common cyber threats:
- Malware: Malicious software designed to disrupt, damage, or gain unauthorized access to computer systems.
- Phishing: Deceptive attempts to acquire sensitive information, such as usernames, passwords, and credit card details, by disguising as a trustworthy entity.
- Ransomware: A type of malware that encrypts a victim’s files and demands a ransom to restore access.
- DDoS Attacks: Overwhelming a network or server with a flood of traffic, making it unavailable to legitimate users.
- Man-in-the-Middle Attacks: Intercepting communication between two parties to eavesdrop or manipulate the information being exchanged.
- SQL Injection: Exploiting vulnerabilities in database-driven applications to gain unauthorized access to sensitive data.
- Zero-Day Exploits: Attacks that target vulnerabilities that are unknown to the software vendor and for which no patch is available.
2. Setting Up Your Cyber Security Learning Environment
To effectively learn cyber security, you need a suitable learning environment. This involves setting up your computer, installing necessary software, and familiarizing yourself with useful tools.
2.1 Hardware and Software Requirements
- Computer: A computer with a modern operating system (Windows, macOS, or Linux) and sufficient processing power (at least 8 GB of RAM and a multi-core processor).
- Virtualization Software: Software like VirtualBox or VMware allows you to run multiple operating systems on a single machine, creating isolated environments for testing and experimentation.
- Text Editor: A robust text editor such as VSCode, Sublime Text, or Notepad++ for writing and editing code and configuration files.
- Web Browser: Modern web browsers like Chrome, Firefox, or Brave for accessing online resources and testing web security.
2.2 Setting Up a Virtual Lab
A virtual lab is essential for practicing cyber security skills in a safe and controlled environment. Here’s how to set one up:
- Install Virtualization Software: Download and install either VirtualBox or VMware on your computer.
- Download Operating System Images: Obtain ISO images of operating systems like Kali Linux (a popular distribution for penetration testing) and Windows Server.
- Create Virtual Machines: Create new virtual machines in your virtualization software using the downloaded ISO images. Allocate sufficient resources (RAM, storage, and CPU) to each virtual machine.
- Configure Network Settings: Configure the network settings of your virtual machines to allow communication between them while isolating them from your main network.
2.3 Essential Tools for Cyber Security Beginners
- Wireshark: A network protocol analyzer that captures and analyzes network traffic in real-time.
- Nmap: A network scanner used to discover hosts and services on a computer network.
- Metasploit: A penetration testing framework that provides tools for exploiting vulnerabilities and testing security controls.
- Burp Suite: A web application security testing tool used to identify and exploit vulnerabilities in web applications.
- OWASP ZAP: An open-source web application security scanner that helps you find security vulnerabilities in web applications.
3. Fundamental Cyber Security Concepts
Understanding core cyber security concepts is essential for building a solid foundation. These concepts will help you grasp more advanced topics and apply your knowledge effectively.
3.1 Networking Basics
Networking is the backbone of cyber security. You should be familiar with:
- TCP/IP Model: Understanding the layers of the TCP/IP model (Application, Transport, Network, and Link) and their respective protocols.
- IP Addressing: Knowing how IP addresses are assigned, subnetting, and routing.
- Network Protocols: Familiarizing yourself with common network protocols like HTTP, HTTPS, DNS, SMTP, and SSH.
3.2 Operating System Basics
Operating systems (OS) are the foundation upon which all applications and services run. Understanding OS concepts is crucial for identifying and mitigating security vulnerabilities.
- Windows: Knowledge of Windows architecture, user account management, file system permissions, and the Windows Registry.
- Linux: Understanding Linux distributions, the command-line interface (CLI), file permissions, and package management.
3.3 Cryptography
Cryptography is the art and science of secure communication. It involves techniques for encrypting and decrypting data to protect its confidentiality and integrity.
- Encryption Algorithms: Familiarizing yourself with symmetric encryption algorithms like AES and DES, as well as asymmetric encryption algorithms like RSA and ECC.
- Hashing Algorithms: Understanding hashing algorithms like SHA-256 and MD5, which are used to create unique fingerprints of data for integrity checks.
- Digital Signatures: Learning how digital signatures are used to verify the authenticity and integrity of digital documents.
3.4 Security Policies and Compliance
Security policies are the rules and guidelines that organizations implement to protect their assets and data. Compliance involves adhering to industry regulations and standards.
- Security Policies: Understanding the importance of security policies, including acceptable use policies, password policies, and incident response plans.
- Compliance Standards: Familiarizing yourself with compliance standards like GDPR, HIPAA, PCI DSS, and ISO 27001.
4. Practical Skills for Cyber Security Beginners
Once you have a grasp of the fundamental concepts, it’s time to develop practical skills through hands-on exercises and projects.
4.1 Network Scanning and Reconnaissance
Network scanning and reconnaissance involve gathering information about target systems and networks to identify potential vulnerabilities.
- Nmap: Using Nmap to scan networks, identify open ports, and determine the operating systems and services running on target hosts.
- Recon-ng: Utilizing Recon-ng, a web reconnaissance framework, to gather information about websites, email addresses, and social media profiles.
- The Harvester: Employing the Harvester to collect email addresses, subdomains, and employee names from public sources.
4.2 Web Application Security
Web applications are a common target for cyber attacks. Learning how to identify and exploit web vulnerabilities is essential for protecting web-based systems.
- OWASP ZAP: Using OWASP ZAP to scan web applications for common vulnerabilities like SQL injection, cross-site scripting (XSS), and cross-site request forgery (CSRF).
- Burp Suite: Employing Burp Suite to intercept and analyze web traffic, perform vulnerability scanning, and conduct penetration testing.
4.3 Penetration Testing
Penetration testing involves simulating cyber attacks to identify weaknesses in systems and networks.
- Metasploit: Utilizing Metasploit to exploit vulnerabilities, gain access to target systems, and conduct post-exploitation activities.
- Manual Exploitation: Learning how to manually exploit vulnerabilities by writing custom exploits and payloads.
4.4 Digital Forensics
Digital forensics involves the investigation and analysis of digital evidence to identify the cause and scope of a cyber incident.
- Disk Imaging: Creating forensic images of hard drives and other storage media using tools like dd and FTK Imager.
- Log Analysis: Analyzing system logs, application logs, and network traffic to identify suspicious activity and determine the timeline of events.
5. Building a Portfolio and Getting Certified
As you gain skills and experience in cyber security, it’s important to build a portfolio of your work and pursue relevant certifications to validate your expertise.
5.1 Creating a Portfolio
A portfolio is a collection of projects, write-ups, and other materials that demonstrate your skills and abilities in cyber security.
- Capture the Flag (CTF) Challenges: Participating in CTF competitions and documenting your solutions to showcase your problem-solving skills.
- Personal Projects: Developing your own cyber security tools, scripts, or applications and sharing them on platforms like GitHub.
- Blog Posts: Writing blog posts or articles about cyber security topics to demonstrate your knowledge and communication skills.
- Vulnerability Disclosures: Reporting vulnerabilities you discover in software or web applications to the vendor and publicly disclosing them (with permission) to demonstrate your ethical hacking skills.
5.2 Popular Cyber Security Certifications
Cyber security certifications can enhance your credibility and demonstrate your expertise to potential employers. Some popular certifications include:
- CompTIA Security+: A foundational certification that covers essential security concepts and practices.
- Certified Ethical Hacker (CEH): A certification that focuses on ethical hacking techniques and penetration testing.
- Certified Information Systems Security Professional (CISSP): A certification for experienced security professionals that covers a wide range of security topics.
- GIAC Certifications: A range of specialized certifications in areas like penetration testing, digital forensics, and incident response.
6. Staying Updated with the Latest Trends
Cyber security is a constantly evolving field, so it’s important to stay updated with the latest trends, threats, and technologies.
6.1 Following Industry News and Blogs
- Security Blogs: Reading security blogs like Krebs on Security, Dark Reading, and The Hacker News to stay informed about current events and emerging threats.
- Industry Publications: Subscribing to industry publications like CSO Online, Security Magazine, and InfoSecurity Magazine to get in-depth analysis and insights.
6.2 Participating in Communities and Forums
- Online Forums: Engaging in online forums like Reddit’s r/cybersecurity and Stack Exchange’s Information Security to ask questions, share knowledge, and network with other professionals.
- Local Meetups: Attending local cyber security meetups and conferences to learn from experts and connect with peers.
6.3 Continuous Learning and Professional Development
- Online Courses: Enrolling in online courses on platforms like Coursera, Udemy, and LEARNS.EDU.VN to expand your knowledge and skills.
- Conferences and Workshops: Attending cyber security conferences and workshops to learn about the latest technologies and best practices.
7. Ethical Considerations in Cyber Security
Ethical considerations are crucial in cyber security. As you learn and develop your skills, it’s essential to understand the ethical implications of your actions and adhere to ethical principles.
7.1 Legal Boundaries
- Computer Fraud and Abuse Act (CFAA): Understanding the CFAA, which prohibits unauthorized access to computer systems and data.
- Digital Millennium Copyright Act (DMCA): Familiarizing yourself with the DMCA, which addresses copyright issues in the digital age.
7.2 Ethical Hacking
Ethical hacking involves using hacking techniques to identify vulnerabilities and improve security with the permission of the system owner.
- Informed Consent: Obtaining informed consent from the system owner before conducting any security testing or vulnerability assessments.
- Scope of Engagement: Defining the scope of engagement with the system owner to ensure that testing activities are conducted within agreed-upon boundaries.
- Confidentiality: Maintaining the confidentiality of sensitive information discovered during security testing and vulnerability assessments.
7.3 Responsible Disclosure
Responsible disclosure involves reporting vulnerabilities to the vendor in a timely manner and allowing them a reasonable period to address the issue before publicly disclosing it.
- Vulnerability Reporting: Following the vendor’s vulnerability reporting process and providing them with detailed information about the vulnerability.
- Disclosure Timeline: Adhering to a responsible disclosure timeline to give the vendor time to develop and release a patch before publicly disclosing the vulnerability.
8. Career Paths in Cyber Security
Cyber security offers a wide range of career paths, each with its own set of responsibilities and requirements.
8.1 Security Analyst
Security analysts are responsible for monitoring security systems, analyzing security incidents, and implementing security measures to protect organizations from cyber threats.
- Responsibilities: Monitoring security systems, analyzing security incidents, conducting vulnerability assessments, and implementing security measures.
- Skills: Knowledge of security tools, understanding of network protocols, and ability to analyze security logs.
8.2 Penetration Tester
Penetration testers simulate cyber attacks to identify vulnerabilities in systems and networks.
- Responsibilities: Conducting penetration tests, identifying vulnerabilities, and providing recommendations for remediation.
- Skills: Expertise in penetration testing tools, understanding of common vulnerabilities, and ability to write custom exploits.
8.3 Security Engineer
Security engineers design, implement, and manage security systems and infrastructure.
- Responsibilities: Designing security systems, implementing security controls, and managing security infrastructure.
- Skills: Knowledge of security technologies, understanding of network architecture, and ability to configure security devices.
8.4 Security Architect
Security architects are responsible for developing and implementing security strategies and architectures.
- Responsibilities: Developing security strategies, designing security architectures, and providing guidance on security best practices.
- Skills: Knowledge of security frameworks, understanding of risk management, and ability to communicate security requirements to stakeholders.
8.5 Chief Information Security Officer (CISO)
The CISO is responsible for overseeing the organization’s security program and ensuring that security measures are in place to protect the organization’s assets and data.
- Responsibilities: Developing security policies, managing security risks, and overseeing the organization’s security program.
- Skills: Knowledge of security governance, understanding of regulatory requirements, and ability to communicate security risks to executive management.
9. Resources for Cyber Security Beginners
Numerous resources are available to help you learn cyber security, including online courses, books, and websites.
9.1 Online Courses
- Coursera: Offers courses on cyber security fundamentals, network security, and web application security.
- Udemy: Provides a wide range of cyber security courses for beginners and advanced learners.
- LEARNS.EDU.VN: Offers specialized cyber security courses with a focus on practical skills and real-world applications.
- SANS Institute: Offers in-depth training courses and certifications in various cyber security domains.
9.2 Books
- “Security Engineering” by Ross Anderson: A comprehensive guide to the principles and practices of security engineering.
- “Hacking: The Art of Exploitation” by Jon Erickson: A hands-on guide to hacking techniques and exploitation methods.
- “The Web Application Hacker’s Handbook” by Dafydd Stuttard and Marcus Pinto: A comprehensive guide to web application security testing.
9.3 Websites
- OWASP (Open Web Application Security Project): A community-driven project that provides resources and tools for improving web application security.
- NIST (National Institute of Standards and Technology): Provides standards and guidelines for cyber security.
- SANS Institute: Offers free resources, white papers, and articles on cyber security topics.
10. Frequently Asked Questions (FAQ)
10.1 What is Cyber Security?
Cyber security involves protecting computer systems, networks, and data from digital attacks.
10.2 Why is Cyber Security Important?
Cyber security is essential for protecting sensitive information, preventing financial losses, and maintaining the integrity of critical infrastructure.
10.3 What Skills are Needed for Cyber Security?
Essential skills include networking, operating systems, cryptography, and security tools.
10.4 How Can I Start Learning Cyber Security?
Start by understanding basic concepts, setting up a learning environment, and practicing hands-on exercises.
10.5 What are Common Cyber Security Certifications?
Popular certifications include CompTIA Security+, CEH, and CISSP.
10.6 How Can I Stay Updated with Cyber Security Trends?
Follow industry news, participate in communities, and pursue continuous learning.
10.7 What are the Ethical Considerations in Cyber Security?
Adhere to legal boundaries, practice ethical hacking, and follow responsible disclosure principles.
10.8 What Career Paths are Available in Cyber Security?
Career paths include security analyst, penetration tester, security engineer, and security architect.
10.9 Where Can I Find Resources for Learning Cyber Security?
Online courses, books, and websites like LEARNS.EDU.VN offer valuable resources.
10.10 How Long Does It Take to Become Proficient in Cyber Security?
Proficiency varies based on dedication and learning pace, but expect several months to years.
Learning cyber security is a journey that requires dedication, perseverance, and a passion for technology. By following the steps outlined in this guide, you can build a solid foundation in cyber security and pursue a rewarding career in this rapidly growing field. Remember to stay curious, keep learning, and never stop exploring the ever-evolving world of cyber security, especially with the valuable courses and resources available at LEARNS.EDU.VN.
Ready to take the next step in your cyber security education?
Visit LEARNS.EDU.VN today to explore our comprehensive range of cyber security courses and resources. From foundational concepts to advanced techniques, we provide the tools and knowledge you need to succeed in the dynamic world of cyber security. Our expert instructors and hands-on approach ensure you gain practical skills and stay ahead of the latest threats. Start your journey with learns.edu.vn and become a sought-after cyber security professional. Contact us at 123 Education Way, Learnville, CA 90210, United States, or reach out via WhatsApp at +1 555-555-1212. Your future in cyber security starts here!