In today’s digital age, cybersecurity is no longer just a concern for tech companies; it’s a fundamental necessity for everyone. We live in a world where data is paramount, and unfortunately, personal and organizational information is more susceptible to threats than ever before. From large-scale data breaches to individual identity theft, the risks are significant and constantly evolving. Just a few years ago, the WannaCry ransomware attack demonstrated the global reach of cyber threats, encrypting millions of computers and disrupting operations worldwide. Organizations of all sizes, from multinational corporations to local businesses, are in a continuous battle to safeguard their digital assets from cybercriminals. The good news is, understanding and Learning Cyber Security is not only crucial for businesses, but also increasingly important for individuals wanting to protect their digital lives.
Understanding the Fundamentals of Cyber Security
Before diving deeper into learning cyber security, it’s essential to grasp what it truly means. Cybersecurity is the practice of protecting computer systems, networks, and digital data from unauthorized access, damage, or theft. It encompasses technologies, processes, and measures designed to defend against cyber attacks.
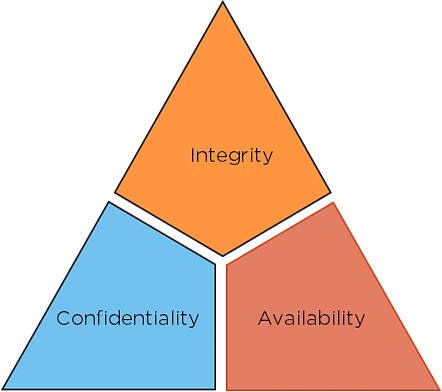
The importance of cybersecurity cannot be overstated. It is vital for national security, healthcare systems, financial institutions, businesses of all sizes, and individuals. In a data-driven world, the exploitation of sensitive information can lead to devastating consequences. To effectively learn and implement cybersecurity strategies, understanding the core principles is key. A foundational concept in cybersecurity is the CIA Triad, which represents the three pillars of information security: Confidentiality, Integrity, and Availability. Let’s explore each of these in the context of learning cyber security.
The CIA Triad: Core Principles of Information Security
The CIA Triad is an industry-standard model that has guided computer security practices since the early days of mainframe computing. It provides a framework for understanding and implementing security policies.
-
Confidentiality: This principle ensures that sensitive information is accessible only to authorized individuals or systems. Think of it as keeping secrets safe. In practice, this means using encryption, access controls, and other measures to prevent unauthorized disclosure of data. For someone learning cyber security, understanding confidentiality is crucial as it underpins data protection strategies.
-
Integrity: Integrity focuses on maintaining the accuracy and completeness of data. It ensures that information is not altered or tampered with by unauthorized parties. This involves implementing measures to prevent data modification, deletion, or fabrication. For learners, grasping integrity is vital for understanding how to ensure data trustworthiness and reliability.
-
Availability: Availability ensures that systems, networks, and data are accessible to authorized users when needed. This principle addresses the prevention of service disruptions and ensures business continuity. It involves implementing measures to protect against denial-of-service attacks, hardware failures, and other events that could impact access to critical resources. For those learning cyber security, availability highlights the importance of system resilience and uptime.
Key Areas to Focus on When Learning Cyber Security
To effectively learn cyber security, it’s helpful to understand the different specializations within the field. These areas represent the diverse skills and knowledge required to protect the digital world. Here are some key domains to consider when focusing your learning:
-
Access Control and Identity Management: This area focuses on methods and systems for controlling who can access what resources. Learning about access control models, authentication methods, and authorization techniques is fundamental to preventing unauthorized access.
-
Network Security: Networks are the backbone of modern communication, and securing them is paramount. Learning network security involves understanding network protocols, firewalls, intrusion detection systems, VPNs, and other technologies used to protect network infrastructure and data flow.
-
Security Management and Risk Assessment: Effective cybersecurity requires strong management practices. This domain involves learning how to develop security policies, conduct risk assessments, implement security frameworks, and manage security incidents.
-
Security Architecture and Design: Building secure systems from the ground up is crucial. This area focuses on learning secure design principles, security models, and how to integrate security into the system development lifecycle.
-
Cyber Law, Ethics, and Investigations: Understanding the legal and ethical landscape of cybersecurity is increasingly important. Learning about cyber law, digital forensics, and ethical hacking practices provides a well-rounded perspective on the field.
-
Application and Software Security: Software vulnerabilities are a major source of cyber attacks. Learning application security involves understanding secure coding practices, vulnerability assessment, penetration testing, and methods to protect software applications from threats.
-
Cryptography: Cryptography is the science of secure communication. Learning cryptography involves understanding encryption algorithms, hashing functions, digital signatures, and their application in securing data and communications.
-
Security Operations and Monitoring: Continuous monitoring and proactive security operations are essential for detecting and responding to threats. Learning security operations involves understanding security monitoring tools, incident response processes, and security information and event management (SIEM) systems.
-
Physical Security: While often overlooked in the digital realm, physical security is still a vital part of cybersecurity. Learning about physical security measures, such as access controls, surveillance systems, and environmental security, ensures a holistic approach to protection.
Essential Terminologies for Cyber Security Learners
To effectively learn cyber security, it’s crucial to become familiar with some basic terminologies. These terms are the building blocks for understanding more complex concepts.
-
Network: At its simplest, a network is a connection between two or more computers that allows them to communicate and share resources. Understanding network fundamentals is essential for grasping many cybersecurity concepts.
-
Internet: The Internet is a global network of networks that connects computers across the world. It utilizes dedicated routers and servers to facilitate communication and data transfer on a massive scale.
-
Internet Protocols: Data transmission over the internet follows specific rules known as internet protocols. These protocols govern how data is formatted, transmitted, and received, ensuring smooth and reliable communication.
-
IP Address (Internet Protocol Address): Every device connected to a computer network and using the Internet Protocol is assigned a unique numerical identifier called an IP address. This address allows devices to locate and communicate with each other on the network. An example of an IP address is
192.168.1.1. -
MAC Address (Media Access Control Address): Each network interface card (NIC) in a device has a unique hardware identifier called a MAC address. This address is used for communication within a local network and is typically represented as a 12-digit hexadecimal number, like
00-1A-2B-3C-4D-5E. -
DNS (Domain Name System): Think of DNS as the internet’s phonebook. It translates human-readable domain names (like
google.com) into IP addresses that computers understand. This system makes it easier for users to access websites and online services.
- DHCP (Dynamic Host Configuration Protocol): DHCP is a network management protocol used to automatically assign IP addresses and other network configuration parameters to devices on a network. This simplifies network administration and ensures efficient IP address allocation.
-
Router: A router is a networking device that forwards data packets between computer networks. Routers analyze destination IP addresses and direct traffic along the most efficient path, ensuring data reaches its intended recipient.
-
Bots: Bots are software applications that perform automated tasks. In a cybersecurity context, “bots” often refer to malicious programs that can control a computer without the user’s knowledge, often used to carry out attacks.
Common Types of Cyber Attacks to Learn About
Understanding the types of attacks is crucial for anyone learning cyber security. Knowing how attacks work and their motivations is the first step in developing effective defenses. The primary motive behind most cyber attacks is financial gain, although attacks can also be driven by political motivations, reputational damage, or disruption. Here are some common types of cyber attacks that learners should be familiar with:
- DDoS (Distributed Denial of Service) Attacks: DDoS attacks aim to overwhelm a target system or network with malicious traffic, making it unavailable to legitimate users. Attackers utilize botnets, networks of compromised computers, to flood the target with requests, causing service disruption.
- Man-in-the-Middle (MitM) Attacks: In a MitM attack, an attacker intercepts communication between two parties without their knowledge. This allows the attacker to eavesdrop on, steal, or manipulate data being exchanged. Public Wi-Fi networks are common environments for MitM attacks.
-
Password Attacks: Password attacks aim to compromise user credentials. Common methods include:
- Dictionary Attacks: Using lists of common passwords to guess user accounts.
- Brute Force Attacks: Trying every possible combination of characters to crack a password.
- Keyloggers: Software or hardware that records keystrokes, capturing passwords as they are typed.
- Shoulder Surfing: Observing someone entering their password over their shoulder.
- Rainbow Tables: Precomputed tables used to reverse hash functions and recover passwords.
-
Email Attacks: Email is a common vector for cyber attacks. Types of email attacks include:
- Phishing: Deceptive emails designed to trick recipients into revealing sensitive information like passwords or credit card details. These emails often mimic legitimate organizations.
- **Spoofing:** Forging the sender address in an email to appear as if it originated from a trusted source. This is often used in phishing and other malicious campaigns.- **Malicious Attachments:** Emails containing infected files as attachments. Opening these attachments can lead to malware infections.- Malware Attacks: Malware (malicious software) encompasses various types of harmful software designed to infiltrate and damage computer systems. Common types include:
- Viruses: Malware that attaches itself to legitimate files and spreads when those files are executed. Viruses often require human action to propagate.
- Worms: Standalone malware programs that can self-replicate and spread across networks without human intervention.
Functions and Sources of Malware: What Learners Need to Know
Understanding how malware functions and how systems get infected is vital for learning effective cybersecurity practices.
Functions of Malware:
-
Resource Overwhelm: Malware, particularly worms, can consume excessive system resources, leading to performance degradation and system crashes.
-
Backdoor Creation: Malware can create backdoors, allowing attackers to bypass normal security measures and gain persistent access to compromised systems.
-
Security Function Disablement: Some malware is designed to disable antivirus software, firewalls, and security updates, making the system more vulnerable to further attacks.
-
Botnet Creation: Malware can turn infected computers into bots, which are then controlled by a botmaster to launch large-scale attacks like DDoS attacks.
Sources of Malware Infections:
-
Removable Media: USB drives, external hard drives, and other removable media can be infected with malware and spread it to systems when connected.
-
Infected Files: Documents and executable files downloaded from untrusted sources or received as email attachments can contain malware.
-
Internet Downloads: Downloading software or files from untrusted websites increases the risk of malware infection.
-
Unsecured Networks: Connecting to unsecured public Wi-Fi networks can expose devices to malware and other cyber threats.
-
Malicious Advertisements (Malvertising): Clicking on compromised or malicious online advertisements can lead to malware downloads or redirects to phishing websites.
Exploring Cyber Security Job Roles for Aspiring Professionals
For those learning cyber security with career aspirations, understanding the different job roles in the field is important. The cybersecurity field offers a wide range of specializations and career paths. Here are some prominent job roles:
-
Chief Information Security Officer (CISO): The CISO is responsible for overseeing an organization’s entire information security program, developing security strategies, and ensuring compliance.
-
Forensic Computer Analyst: These professionals investigate cyber incidents, analyze digital evidence, and help organizations recover from attacks and prevent future incidents.
-
Information Security Analyst: Information security analysts plan and implement security measures to protect computer systems and networks. They monitor for threats, conduct vulnerability assessments, and respond to security incidents.
-
Penetration Tester (Ethical Hacker): Penetration testers simulate cyber attacks to identify vulnerabilities in systems and networks. They provide valuable insights into security weaknesses and recommend remediation strategies.
-
IT Security Engineer: IT security engineers design, implement, and manage security systems and technologies. They focus on the technical aspects of security, such as firewalls, intrusion detection systems, and security infrastructure.
-
Security Architect: Security architects design and plan the overall security architecture of an organization’s IT systems. They define security requirements, select security technologies, and ensure that security is integrated into all aspects of IT infrastructure.
-
Security Systems Administrator: Security systems administrators are responsible for the day-to-day operation and maintenance of security systems. They install, configure, and troubleshoot security software and hardware.
-
IT Security Consultant: IT security consultants provide expert advice and guidance to organizations on cybersecurity matters. They assess security risks, recommend security solutions, and help organizations improve their security posture.
Cyber Security Certifications to Enhance Your Learning Journey
For individuals serious about learning cyber security and pursuing a career in the field, certifications are highly valuable. They demonstrate knowledge and skills to potential employers and validate expertise. Here are some top cybersecurity certifications for beginners and experienced professionals:
- CompTIA Security+: A foundational certification that validates core security skills and knowledge, covering a broad range of security topics.
- Certified Information Systems Security Professional (CISSP): A globally recognized certification for experienced security professionals, focusing on security management and leadership.
- Certified Ethical Hacker (CEH): A certification that focuses on ethical hacking techniques and penetration testing methodologies.
Cybersecurity is a rapidly growing and critically important field. As technology continues to advance, the demand for skilled cybersecurity professionals will only increase. Learning cyber security is not just about acquiring technical skills; it’s about developing a mindset of vigilance, problem-solving, and continuous learning in the face of ever-evolving digital threats. Whether you are an individual looking to protect your personal data or an aspiring professional seeking a rewarding career, embarking on the journey of learning cyber security is a valuable and timely endeavor.